Video surveillance solutions have become very popular during the last years, therefore, we take the task of working these solutions together with the support of different manufacturers, to provide the best service to our customers.
If we talk about business, we can mention that there are intelligence solutions, which provide the most efficient tools for marketing and data analysis, highly accurate, generating invaluable statistics for owners of small and medium enterprises. Through the knowledge of the number of potential customers and detailed information of their traffic, thus improving the management of their business.
We also mentioned the security intelligence application, which not only allows the monitoring of facilities and properties, but also enables the regulation of activities in designated areas and the management of customer waiting time in specific zones and other key business variables. With these advanced functionalities, users can increase security and personalize the business while acquiring the data needed to optimize operations.
Features
- Video surveillance and business intelligence integrated in one camera.
- High level of accuracy.
- Real-time analysis and visualization.
- Direct access through web site.
- Easy configuration.
- Applications embedded in the camera.
- Adaptable applications.
CYBERSECURITY
Cyber security assurance efforts are incorporated into the life cycle of its products, including development, verification, manufacturing, delivery and service. Our manufacturer is constantly evaluating and improving cyber security in order to provide our customers with the highest quality and most reliable products.
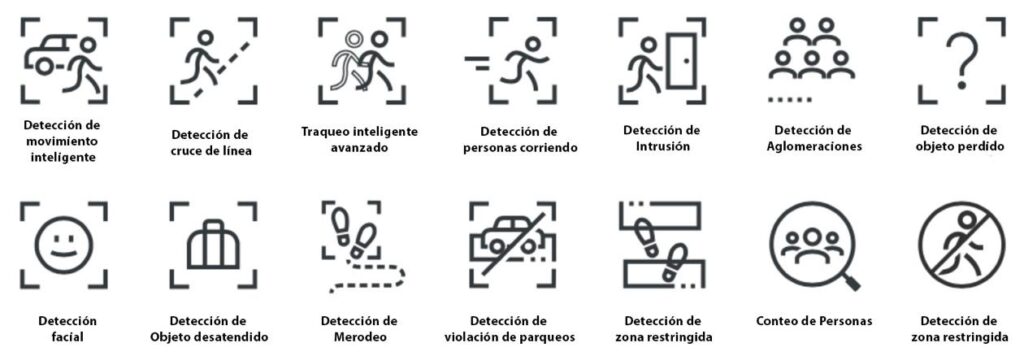
APPLICATIONS
For our business verticals: hospital vertical, industrial, hotel, office, corporate centers, banking, airports and transportation, supermarkets and education, we can use cybersecurity as follows:
Blocking Brute Force Attacks
Brute force attacks based on a certain number of failed login attempts, when this happens a defense mechanism is automatically activated to block the IP address and prevent further attacks.
Intrusion Detection and Prevention
After access to the computer is enabled, if any malware, abnormal behavior, attempt to control the console, access to controversial web pages, or other intrusive behavior is detected it will be automatically secured by the attack mechanism.
Instant Damage Control
If an unknown attack occurs, the system repairs all data remotely and transfers it to the antivirus team to analyze and resolve the problem temporarily, effectively decreasing the spread of internal viruses, allowing users to get back to work safely and quickly.
People counting and capacity
Detailing the number of people entering a site, this application becomes indispensable for the productivity and security of the business as it avoids the saturation of people.
License Plate Recognition
Through the use of cameras, license plates can be captured in real time to monitor the entry and exit of vehicles, as well as during their transit on the streets or highways.
Line Crossing Detection
This refers to the control and monitoring of the entry of people to already established restricted areas, to avoid possible thefts within an enclosure or business, or to avoid unauthorized entry to different areas.
Crowd Detection
We refer to the detection of crowds of people in a certain area, what is intended is to inform in real time the security and administrative staff when such situations occur in order to have a safer and friendlier environment.
Facial recognition detection
It is a novel application of facial biometric identification designed to recognize, verify and give proof of life to a user; without maintaining personal contact. With this we can prevent fraud, improve the customer experience and make transactions safer.




