Workplace security is no longer an option, but a necessity. Today, having a modern and efficient access control system not only protects people but also optimizes resources and improves internal management for any business.

What is an access control system?
This is a technological solution designed to authorize or restrict access to certain areas, whether within offices, industrial plants, hospitals, educational institutions, or even residential spaces. Its main function is to ensure that only authorized individuals can enter certain locations, significantly increasing security levels.

Types of access control systems
Each company can choose the system that best suits its needs. Here are some of the most commonly used:
🔒 Access with physical credentials
This method requires a card, key fob, or tag that must be scanned by a reader. It is an economical and easy-to-implement option, although it carries certain risks if the devices are lost.
🧬 Biometric access
Through facial, fingerprint, or iris recognition, this system guarantees 100% personalized access. Its security level is very high, as it cannot be falsified or borrowed.
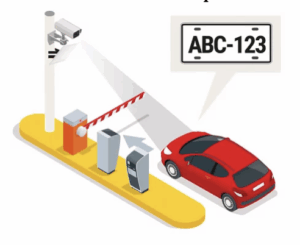
🚗 Vehicle license plate recognition
Ideal for private parking lots or garages, it allows automatic registration of vehicle access using license plate reading cameras.
🌐 Networked vs. Standalone Systems
• Standalone: They don’t require an internet connection and operate locally. They are useful in small spaces or with few users.
• Networked: More advanced, they allow for integrated schedules, reports, and notifications, and can be combined with other systems such as alarms or video surveillance.
Advantages of Implementing Access Control
1. Reduction in Risk and Theft: By limiting who can enter, incidents are minimized.
2. Greater Control Over Visitors and Staff: Precise Tracking of Who Enters, at What Time, and How Long They Stay.
3. Savings in Human Resources: The Need for Physical Security at Entrances and Exits Is Reduced.
4. Management Flexibility: Schedules can be set, temporary access can be blocked, and reports can be generated.
5. Integration with Other Security Tools: Surveillance Cameras, Alarms, or Sensors.
What Components Do These Systems Typically Have?
• Access readers (cards, biometrics)
• Controllers (manage permissions)
• Electromagnetic or electronic locks
• Exit buttons
• Administration software